Be part of our every day and weekly newsletters for the most recent updates and unique content material on industry-leading AI protection. Study Extra
Going into 2025, safeguarding income and minimizing enterprise dangers should dominate CISOs’ budgets, with investments aligned with enterprise operations driving priorities.
Forrester’s newest budget planning guide for security and risk clarifies that securing business-critical IT property must be a excessive precedence going into subsequent yr. “The finances will increase that CISOs will obtain in 2025 ought to prioritize addressing threats and controls in software safety, individuals and business-critical infrastructure,” writes Forrester within the report.
CISOs should double down on threats and controls to get software safety rights, safe business-critical infrastructure and enhance human threat administration. Forrester sees software program provide chain safety, API safety and IoT/OT menace detection as core to enterprise operations and advises CISOs to spend money on these areas.
Delivering income beneficial properties by defending new digital companies whereas preserving IT infrastructure secure on a decent finances is a confirmed approach for CISOs to advance their careers.
Deal with cybersecurity as a enterprise choice first
Essentially the most precious takeaway from Forrester’s planning information is that cybersecurity investments have to be thought of a enterprise choice first. The report’s key findings and tips underscore how and why CISOs must make trade-offs on instruments and spending to maximise income development whereas driving stable returns on their investments.
Forrester requires CISOs to take a tough have a look at any app, software, or suite contributing to tech sprawl and drop it from their tech stacks when including new applied sciences.
Essential insights from Forrester’s finances planning information for safety and threat embody the next:
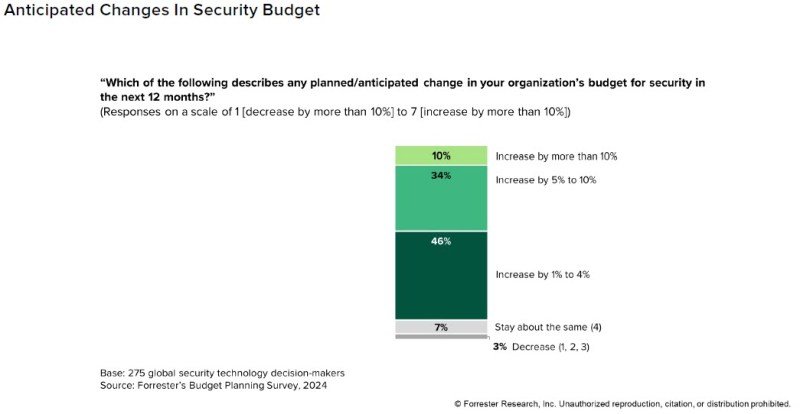
- 90% of CISOs will see a finances enhance subsequent yr. Cybersecurity budgets are, on common, simply 5.7% of IT annual spending. That’s skinny, given how broad a CISO’s position is to guard new income streams and fortify infrastructure. Forrester cites their 2024 Price range Planning Survey 2024 within the information, predicting that budgets will proceed growing for the following 12 months. Ten % anticipate a rise of greater than 10% within the subsequent 12 months. One-third count on a rise between 5% and 10%, and virtually half count on a modest enhance between 1% and 4%. Solely seven % of the budgets will keep the identical, and simply three % anticipate diminished budgets in 2025.

- Get accountable for tech sprawl now. Tech sprawl is the silent killer of finances beneficial properties, Forrester warns. CISOs, on common, are seeing simply over a 3rd of their budgets come from software program, doubling what they spend on {hardware} and in addition outpacing their personnel prices, in accordance with a current ISG study. “To fight the real difficulty that already plagues safety leaders — tech sprawl — we advocate taking a conservative method to introducing new instruments and distributors with this pragmatic precept: Don’t add one thing new with out eliminating one thing else first,” writes Forrester within the report.

Supply: Forrester 2025 Price range Planning Information For Safety And Danger Leaders
- Cloud safety, upgraded new safety know-how run on-premises, and safety consciousness/coaching initiatives are predicted to extend safety budgets by 10% or extra in 2025. Notably, 81% of safety know-how decision-makers predict their spending on cloud safety will enhance in 2025, with 37% anticipating a 5-10% enhance and 30% anticipating a greater than 10% enhance. Cloud safety’s excessive precedence displays the important position that cloud environments, platforms, and integrations play within the general safety posture of enterprises. As extra enterprises undertake and construct inside platforms and apps throughout IaaS, PaaS, and SaaS, cloud safety spending will proceed to develop.

Defending income begins with APIs and software program provide chains
A core a part of each CISO’s job is discovering new methods to guard income, particularly digital-first initiatives enterprise devops groups are working time beyond regulation to get out this yr.
Listed below are their prompt priories from the report:
Hardening software program provide chain and API safety is a must have. Making the argument that the complexity, selection and quantity of assault surfaces are proliferating throughout software program provide chains and API repositories, Forrester emphasizes that safety is urgently wanted in these two areas. A staggering 91% of enterprises have fallen sufferer to software program provide chain incidents in only a yr, underscoring the necessity for higher safeguards for steady integration/deployment (CI/CD) pipelines. Open-source libraries, third-party improvement instruments, and legacy APIs created years in the past are just some menace vectors that make software program provide chains and APIs extra weak.
Malicious attackers usually look to compromise open-source elements with vast distribution, because the Log4j vulnerability illustrates. Defining an API security strategy that integrates straight into DevOps workflows and treats the continual integration and steady supply (CI/CD) course of as a novel menace floor is desk stakes for any enterprise doing DevOps at this time. API detection and response, remediation insurance policies, threat evaluation, and API utilization monitoring are additionally pressing for enterprises to raised safe this potential assault vector.
IoT sensors proceed to be an assault magnet
Web of Issues (IoT) is the most well-liked assault vector attackers use to assault industrial management programs (ICS) and the numerous processing crops, distribution facilities and manufacturing facilities that depend on them every day. CISA continues to warn that nation-state actors are focusing on weak industrial management property and at this time three new industrial control systems advisories have been printed by the company.
Forrester’s Top Trends In IoT Security In 2024, printed earlier this yr and lined by VentureBeat, discovered that 34% of enterprises that skilled a breach focusing on IoT units have been extra prone to report cumulative breach prices between $5 million and $10 million in comparison with organizations that skilled cyberattacks on non-IoT units.
“In 2024, the potential of IoT innovation is nothing in need of transformative. However together with alternative comes threat. Every related gadget presents a possible entry level for a malicious actor,” writes Ellen Boehm, senior vp of IoT Technique & Operations for Keyfactor. Of their current IoT safety report, Digital Trust in a Connected World: Navigating the State of IoT Security, Keyfactor discovered that 93% of organizations face challenges securing their IoT and related merchandise.
“We’re connecting all these IoT units, and all these connections create vulnerabilities and dangers. I feel with OT cybersecurity, I’d argue the worth at stake and the stakes general may very well be even larger than they’re in relation to IT cybersecurity. When you concentrate on what infrastructure and sorts of property we’re defending, the stakes are fairly excessive,” Kevin Dehoff, president and CEO of Honeywell Connected Enterprise, instructed VentureBeat throughout an interview final yr.
“Most prospects are nonetheless studying in regards to the state of affairs of their OT networks and infrastructure. And I feel there’s some awakening that will probably be carried out. We’re offering a real-time view of OT cyber threat” Dehoff stated.
Making certain IoT gadget entry is protected utilizing zero belief is a desk stake for lowering the specter of breaches. The National Institute of Standards and Technology (NIST) gives NIST Special Publication 800-207, which is well-suited for securing IoT units, given its concentrate on securing networks the place conventional perimeter-based safety isn’t scaling as much as the problem of defending each endpoint.
Pragmatism must dominate CISOs’ budgets in 2025
“Too many instruments, too many applied sciences and never almost sufficient individuals proceed to be the theme in a fragmented and technology-heavy cybersecurity vendor ecosystem,” Forrester cautions.
Treating cybersecurity spending as a enterprise funding first is a precedence Forrester sees its shoppers needing to embrace extra, given how that message is emphasised all through the information. The message is to trim again on tech sprawl, which they’ve delivered earlier than concerning the necessity to consolidate cybersecurity apps, instruments and suites.
It’s time for cybersecurity to be funded as a development engine, not only one used for deterrence alone.
CISOs can steadiness the scales by on the lookout for a possibility to raise their position to a CEO direct report and, ideally, be on the board to assist information their firms by an more and more advanced menace panorama.
Source link

bfkj9a
Amazing service, saved us so much time and effort. Will recommend to neighbors. Outstanding job team.
bbsaxt
https://t.me/s/pt1win/292
Актуальные рейтинги лицензионных онлайн-казино по выплатам, бонусам, минимальным депозитам и крипте — без воды и купленной мишуры. Только площадки, которые проходят живой отбор по деньгам, условиям и опыту игроков.
Следить за обновлениями можно здесь: https://t.me/s/reitingcasino
https://t.me/iGaming_live/4570
https://t.me/s/iGaming_live/4547
https://t.me/reyting_topcazino/16
https://t.me/s/reyting_topcazino/23
Thông qua hệ thống tường lửa WAF 5 lớp và công nghệ mã xác thực 2AF, link 188v ẩn danh tuyệt đối mọi tài khoản người chơi đồng thời, mã hóa toàn bộ hoạt động khi hội viên truy cập, sử dụng dịch vụ, sản phẩm. Vì thế, bạn hoàn toàn có thể yên tâm khi cá cược tại đây.
Một trong những yếu tố quan trọng nhất mà rtp slot365 luôn chú trọng là tính an toàn và bảo mật. Mọi thông tin cá nhân tài chính được ngăn chặn sự xâm nhập của hacker. Không chỉ vậy, sân chơi còn tuân thủ các quy định nghiêm ngặt về bảo mật chống rửa tiền, đảm bảo mọi giao dịch của người chơi đều được thực hiện một cách minh bạch an toàn.
Một trong những yếu tố quan trọng nhất mà rtp slot365 luôn chú trọng là tính an toàn và bảo mật. Mọi thông tin cá nhân tài chính được ngăn chặn sự xâm nhập của hacker. Không chỉ vậy, sân chơi còn tuân thủ các quy định nghiêm ngặt về bảo mật chống rửa tiền, đảm bảo mọi giao dịch của người chơi đều được thực hiện một cách minh bạch an toàn.
https://t.me/of_1xbet/801
ưu đãi 188v Sau khi điền xong các thông tin cần thiết, bạn cần kiểm tra lại để đảm bảo không có sai sót. Tiếp theo, bạn sẽ nhấn vào nút “Đăng ký” để hoàn tất quá trình. Một số trường hợp, hệ thống có thể yêu cầu xác minh qua mã OTP gửi về số điện thoại hoặc email để tăng cường bảo mật.
https://t.me/s/ef_beef
I do agree with all the ideas you’ve presented in your post. They’re very convincing and will certainly work. Still, the posts are too short for newbies. Could you please extend them a bit from next time? Thanks for the post.
asia slot365 Đối với người chơi mới, nơi đây mang đến chương trình khuyến mãi nạp tiền lần đầu cực kỳ hấp dẫn. Khi làm thao tác này thì hội viên sẽ nhận được một khoản thưởng tương ứng với tỷ lệ phần trăm trên số tiền nạp, thường từ 50% đến 100%.
asia slot365 Đối với người chơi mới, nơi đây mang đến chương trình khuyến mãi nạp tiền lần đầu cực kỳ hấp dẫn. Khi làm thao tác này thì hội viên sẽ nhận được một khoản thưởng tương ứng với tỷ lệ phần trăm trên số tiền nạp, thường từ 50% đến 100%.
This is very interesting, You’re a very skilled blogger. I’ve joined your feed and look forward to seeking more of your wonderful post. Also, I’ve shared your site in my social networks!
https://t.me/s/officials_pokerdom/3540
165gie
Im Bizzo Casino Online zu spielen verspricht damit eine große Menge an Abwechslung mit dem wachsenden Sortiment. Auf diese Weise lässt sich mit zusätzlichem Bonusguthaben für eine erfolgte Einzahlung spielen. Zwar können Spieler aus Österreich durchaus im Bizzo Casino kostenlos ohne Anmeldung spielen, aber das ist nur der halbe Spaß. Sie können die Kundenberater entweder über die integrierte Live-Chat Funktion oder per E-Mail unter kontaktieren. Es gilt zu beachten, dass viele Einzahlungsboni an einen Mindesteinzahlungsbetrag geknüpft sind.
Bizzo Casino online bietet eine große Auswahl an Tischspielen, die auch bei vielen Zockern beliebt sind. Croupiers spielen möchten, sollten Sie sich mal im Live Casino auf bizzocasino.com umsehen. Darüber hinaus hält sich das Casino an alle branchenüblichen Richtlinien zum verantwortungsvollen Umgang mit Glücksspielen und bietet eine Reihe von Hilfsmitteln an, um Spielern zu helfen, die mit problematischem Spielverhalten zu kämpfen haben könnten.
References:
https://online-spielhallen.de/nv-casino-bonus-2-000-e-225-freispiele-aktuell/
https://t.me/s/BeEFcAsInO_OffICiALS
https://t.me/s/be_1win/674
I don’t normally comment but I gotta say thankyou for the post on this great one :D.