.fusion-sharing-box-1 .fusion-social-network-icon-tagline{margin-right:0.5em !necessary;}.sharingbox-shortcode-icon-wrapper-1 span a{align-items:middle !necessary;show:flex !necessary;}.sharingbox-shortcode-icon-wrapper-1{justify-content:space-evenly !necessary;}.fusion-sharing-box-1 h4{margin-bottom:0 !necessary;}.fusion-sharing-box-1{flex-direction:row !necessary;border-color:#03a9f4 !necessary;padding-top:5 !necessary;padding-bottom:5 !necessary;padding-left:5 !necessary;padding-right:5 !necessary;border-bottom-width:3 !necessary;border-top-width:3 !necessary;border-left-width:3 !necessary;border-right-width:3 !necessary;}.sharingbox-shortcode-icon-wrapper-1 span:not(.sharingbox-shortcode-icon-separator){padding-top:2 !necessary;padding-bottom:2 !necessary;padding-left:20 !necessary;padding-right:20 !necessary;}.sharingbox-shortcode-icon-wrapper-1 a{colour:#ffffff;}.sharingbox-shortcode-icon-wrapper-1 a:hover{colour:#f5f5f5;}.sharingbox-shortcode-icon-wrapper-1 span.sharingbox-shortcode-icon-separator{border-right-width:0px !necessary;}@media solely display and (max-width:1024px){.fusion-sharing-box-1 h4{margin-right:0.5em !necessary;margin-bottom:0 !necessary;}.sharingbox-shortcode-icon-wrapper-1{width:auto !necessary;justify-content:space-evenly !necessary;}.fusion-sharing-box-1{align-items:middle !necessary;} }@media solely display and (max-width:640px){.fusion-sharing-box-1{flex-direction: column !necessary;align-items:middle !necessary;}.fusion-sharing-box-1 h4{margin-bottom:revert !necessary;}.sharingbox-shortcode-icon-wrapper-1{width:100% !necessary;justify-content:space-between !necessary;} }
SOC 2 isn’t just one other compliance checkbox—it’s a trust-building framework designed to make sure that service suppliers handle information securely, safeguarding the pursuits of their purchasers and stakeholders. It focuses on how firms ought to handle information to guard the privateness and pursuits of their purchasers. SOC 2 automation makes use of AI and automation instruments to automate repeatable compliance duties and provides you a real-time, 24×7, steady monitoring. AutomationEdge enhances your SOC 2 compliance posture by way of pre-built controls and real-time, steady compliance monitoring.
What Is SOC 2 Compliance?
SOC 2 (System and Group Controls 2) is a framework developed by the American Institute of Licensed Public Accountants (AICPA). It’s particularly designed for service organizations that deal with or retailer buyer information within the cloud. Not like prescriptive requirements like ISO 27001, SOC 2 is principles-based, which permits flexibility in implementation primarily based on the group’s particular programs and practices.
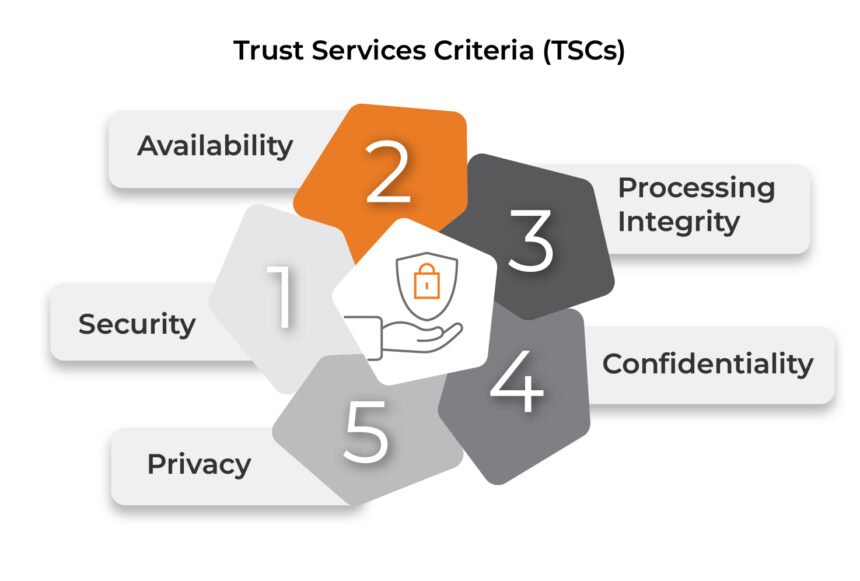
SOC 2 audits are primarily based on 5 Belief Companies Standards (TSCs):
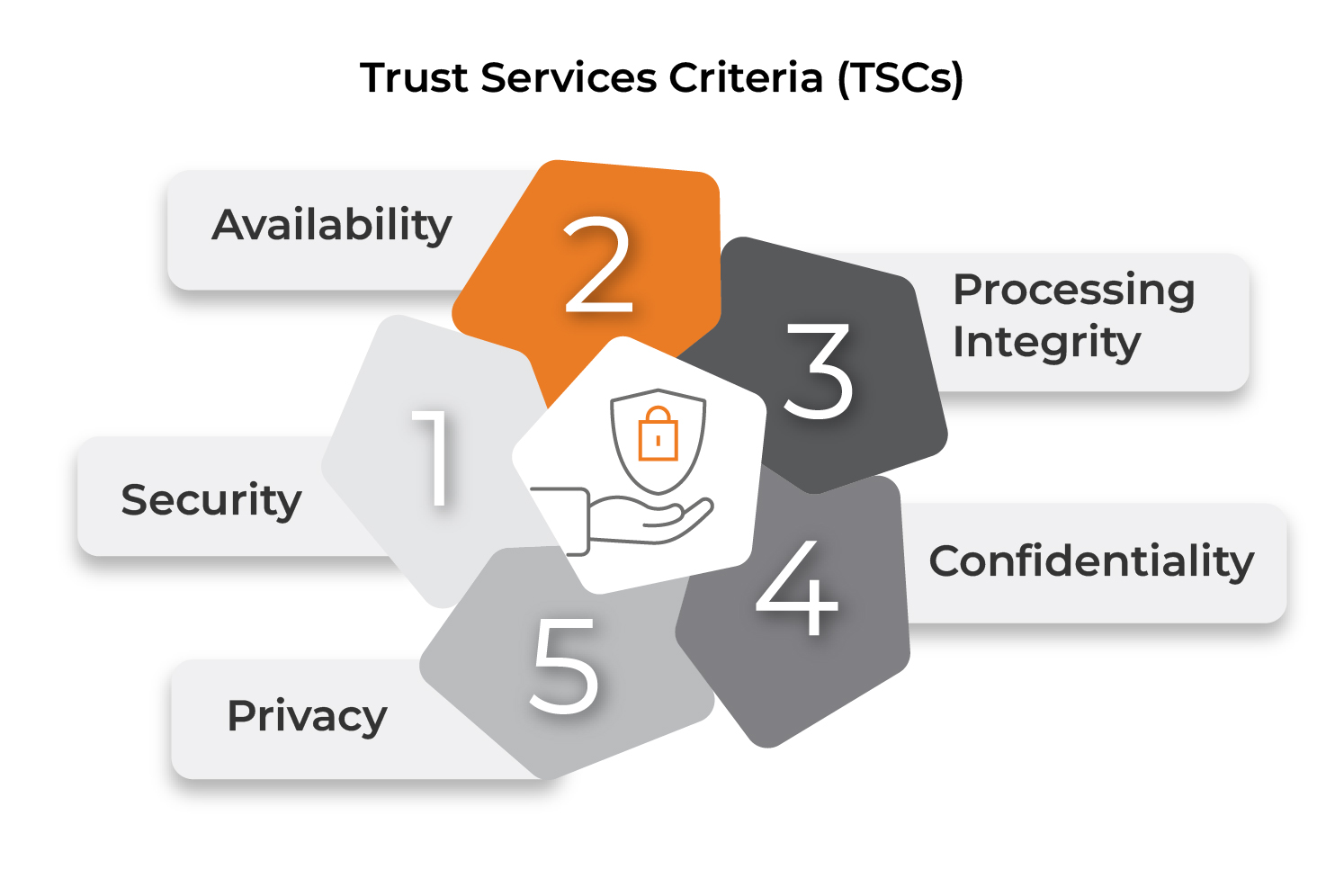
- Safety – Safety of system assets from unauthorized entry.
- Availability – Accessibility of the system as agreed by contract or service-level settlement (SLA).
- Processing Integrity – Assurance that programs course of information precisely, utterly, and on time.
- Confidentiality – Safety of delicate data as dedicated or agreed.
- Privateness – Acceptable assortment, use, retention, and disposal of non-public data.
Find out how to Automate your SOC 2 Compliance
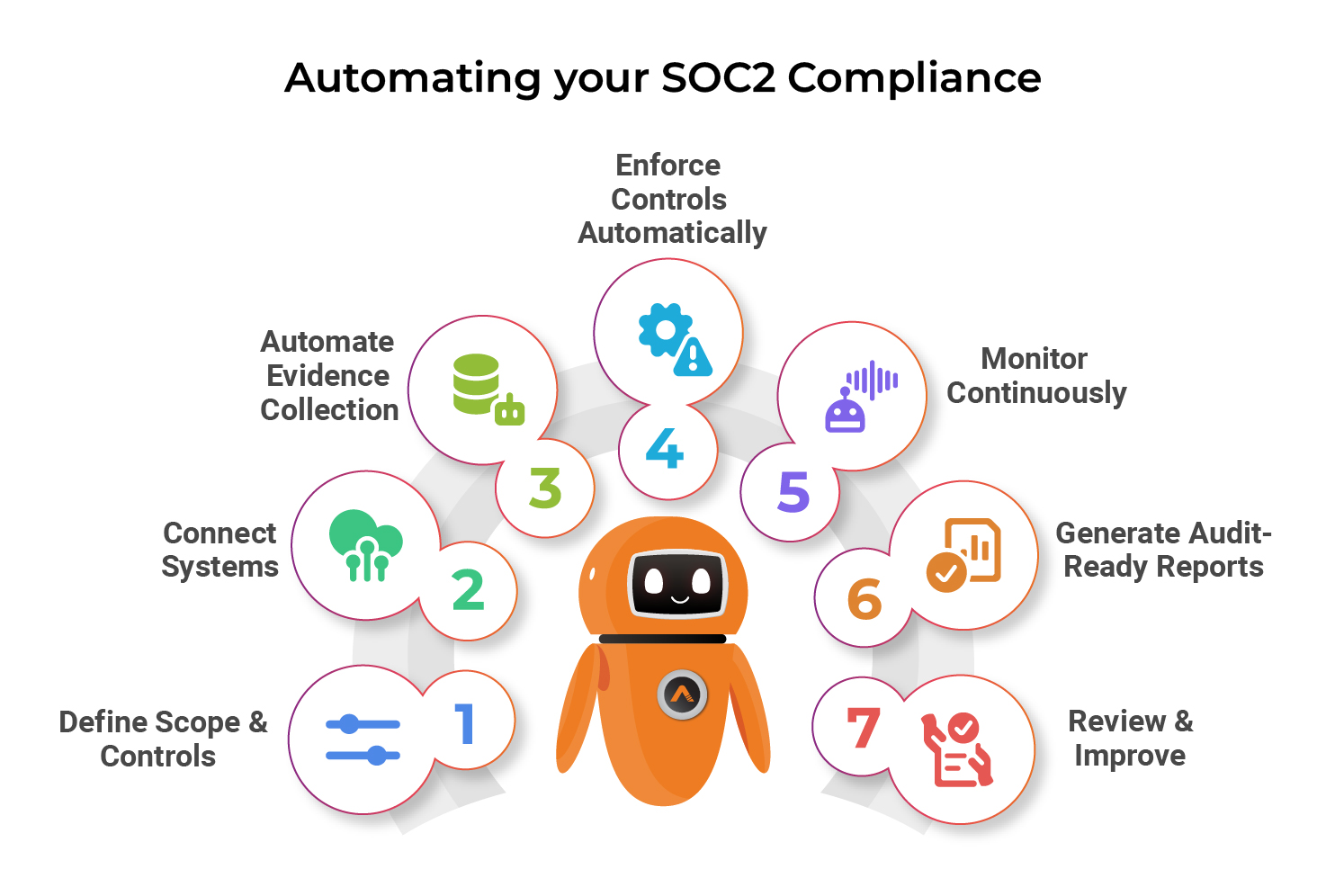
Automating SOC 2 compliance means utilizing software program, bots, and AI to deal with repetitive, time-consuming duties. Right here’s the way it usually works:
-
Outline Scope & Controls
What to do:
Establish which programs, processes, and information fall below SOC 2 (like cloud apps, person entry, information dealing with). Arrange the safety and privateness controls required by SOC 2 (e.g., entry restrictions, audit logs). -
Join Your Programs
What to do:
Combine your cloud companies (AWS, Azure, GCP), HR programs, ticketing instruments, and identification suppliers (like Okta or Energetic Listing) with the automation platform. This enables automated monitoring and information assortment. -
Automate Proof Assortment
What to do:
Arrange bots or scripts to routinely gather proof (like person logs, system modifications, entry data) and retailer it in a central, audit-ready format.
-
Implement Controls Routinely
What to do:
Apply guidelines that auto-enforce compliance insurance policies (like locking inactive accounts, alerting on permission modifications, blocking unauthorized entry). -
Monitor Constantly
What to do:
Use AI and monitoring instruments to maintain watch over your programs 24/7. Get alerts for suspicious actions or coverage violations—earlier than they change into audit points. -
Generate Audit-Prepared Experiences
What to do:
Routinely create and replace reviews that auditors want — with timestamps, logs, and screenshots — all organized and updated.
-
Overview & Enhance
What to do:
Repeatedly evaluation automated reviews and alerts to enhance controls. Replace your insurance policies as your programs and dangers evolve.
Bonus! Make Use of AutomationEdge for Finish-to-Finish SOC 2 Automation. AutomationEdge offers pre-built compliance workflows, AI-driven threat detection, and seamless integration along with your IT and cloud instruments — serving to you keep compliant, on a regular basis.
.fusion-body .fusion-builder-column-3{width:100% !necessary;margin-top : 0px;margin-bottom : 20px;}.fusion-builder-column-3 > .fusion-column-wrapper {padding-top : 0px !necessary;padding-right : 0px !necessary;margin-right : 1.92%;padding-bottom : 0px !necessary;padding-left : 0px !necessary;margin-left : 1.92%;}@media solely display and (max-width:1024px) {.fusion-body .fusion-builder-column-3{width:100% !necessary;order : 0;}.fusion-builder-column-3 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}@media solely display and (max-width:640px) {.fusion-body .fusion-builder-column-3{width:100% !necessary;order : 0;}.fusion-builder-column-3 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}
.fusion-body .fusion-flex-container.fusion-builder-row-4{ padding-top : 0px;margin-top : 0px;padding-right : 0px;padding-bottom : 0px;margin-bottom : 0px;padding-left : 0px;}
What will be Automated with SOC 2 Compliance?
SOC 2 compliance includes steady processes corresponding to information monitoring, proof assortment, entry controls, and threat assessments.
-
Actual-Time Safety Oversight
Conventional compliance strategies depend on periodic checks (month-to-month, quarterly, or yearly), which solely provide a snapshot of your safety posture. SOC 2 automation modifications that with 24/7, real-time monitoring.
Key Advantages:
- Steady surveillance of your programs
- Rapid alerts for:
- Threats
- Coverage violations
- Configuration modifications
- System vulnerabilities
- Sooner response to incidents — earlier than they change into breaches
- Decrease threat and diminished remediation prices
By detecting points in real-time somewhat than throughout quarterly or annual evaluations, organizations can reply to safety incidents earlier than they escalate into information breaches or compliance violations, considerably lowering each threat publicity and potential remediation prices.
-
Streamlined Threat Evaluation and Administration
SOC 2 compliance automation platforms centralize threat administration by way of built-in threat registers that function complete repositories for figuring out, monitoring, and managing safety dangers throughout your group.
The way it works:
- Routinely identifies and logs safety dangers
- Maintains a threat register to trace and handle every subject
- Generates automated threat assessments aligned with SOC 2 controls
- Assigns remediation duties to the proper staff members
- Tracks job progress and shops all documentation
The platform assigns these duties to applicable staff members, tracks progress towards decision and maintains detailed documentation of all threat administration actions. This systematic method ensures that when your annual SOC 2 audit arrives, all mandatory documentation, proof, and remediation data are already compiled and audit-ready, dramatically lowering the effort and time required for audit preparation.
-
Automated Id and Entry Governance
Compliance automation platforms combine subtle identification and entry administration capabilities that standardize and automate the whole worker entry lifecycle.
One of many largest compliance dangers is who has entry to what — particularly when workers be a part of, change roles, or go away the corporate.
What automation does:
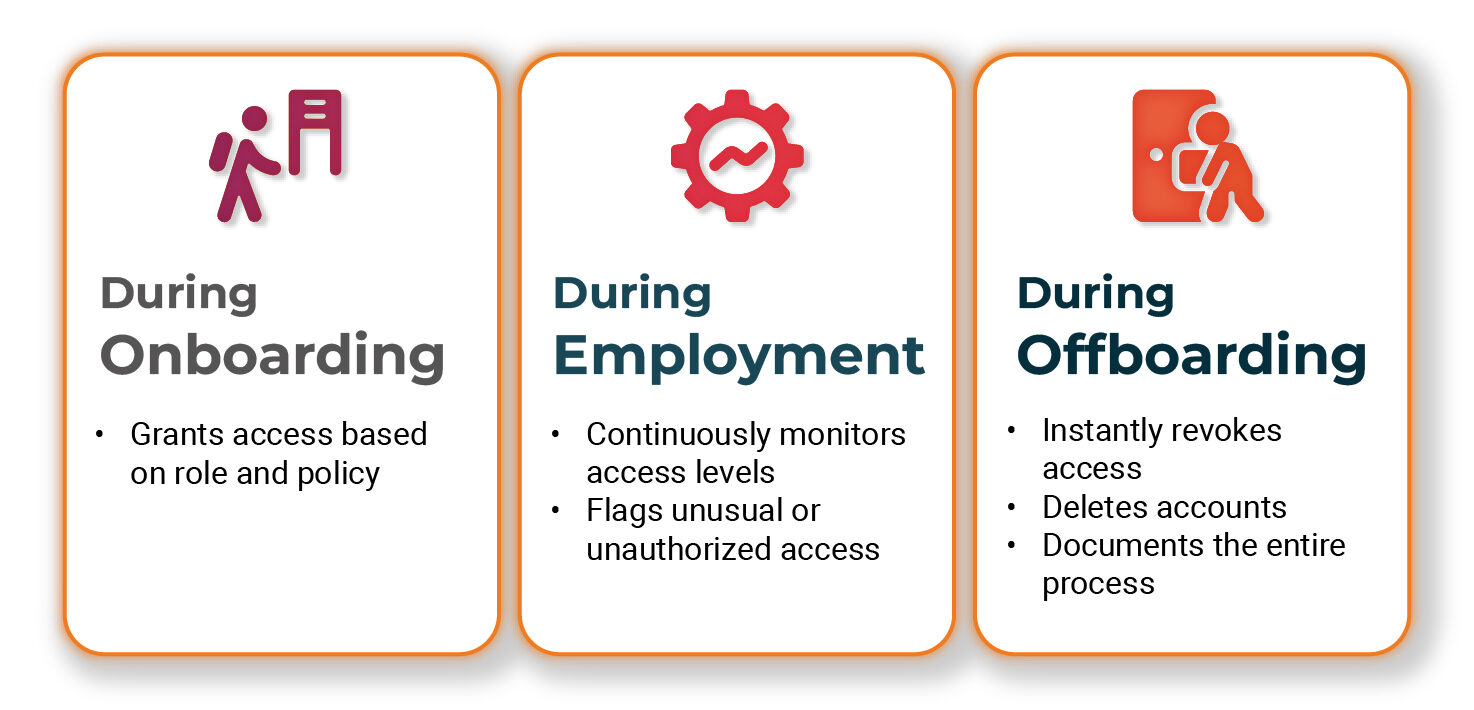
- Throughout onboarding:
- Grants entry primarily based on position and coverage
- Throughout employment:
- Constantly displays entry ranges
- Flags uncommon or unauthorized entry
- Throughout offboarding:
- Immediately revokes entry
- Deletes accounts
- Paperwork the whole course of
This automation eliminates human error in entry administration whereas making certain constant software of safety insurance policies throughout all personnel modifications.
- Throughout onboarding:
-
Clever Vulnerability Detection and Remediation
Compliance automation platforms like AutomationEdge combine with main vulnerability scanning instruments and cloud safety companies to repeatedly assess your expertise infrastructure for safety gaps, misconfigurations, and potential assault vectors.
Capabilities:
- Run steady vulnerability scans
- Establish and prioritize dangers by severity and impression
- Routinely create remediation duties for the IT/safety staff
- Observe subject decision in a dashboard
- Generate real-time reviews for auditors
These platforms present built-in dashboards that show vulnerability standing throughout your total expertise stack, monitor remediation progress, and generate compliance reviews demonstrating your proactive safety administration method to auditors and stakeholders.
.fusion-body .fusion-builder-column-5{width:100% !necessary;margin-top : 0px;margin-bottom : 20px;}.fusion-builder-column-5 > .fusion-column-wrapper {padding-top : 0px !necessary;padding-right : 0px !necessary;margin-right : 1.92%;padding-bottom : 0px !necessary;padding-left : 0px !necessary;margin-left : 1.92%;}@media solely display and (max-width:1024px) {.fusion-body .fusion-builder-column-5{width:100% !necessary;order : 0;}.fusion-builder-column-5 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}@media solely display and (max-width:640px) {.fusion-body .fusion-builder-column-5{width:100% !necessary;order : 0;}.fusion-builder-column-5 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}
.fusion-body .fusion-flex-container.fusion-builder-row-6{ padding-top : 0px;margin-top : 0px;padding-right : 0px;padding-bottom : 0px;margin-bottom : 0px;padding-left : 0px;}
Advantages of SOC 2 Compliance Automation
- Lowered Human Error
Handbook compliance processes are liable to oversight. Automation ensures constant, repeatable controls and reduces gaps. - Steady Compliance
Conventional SOC 2 audits present a snapshot in time. Automation allows real-time visibility and steady compliance monitoring. - Decrease Operational Prices
Reduces the necessity for big compliance groups and repetitive handbook duties.
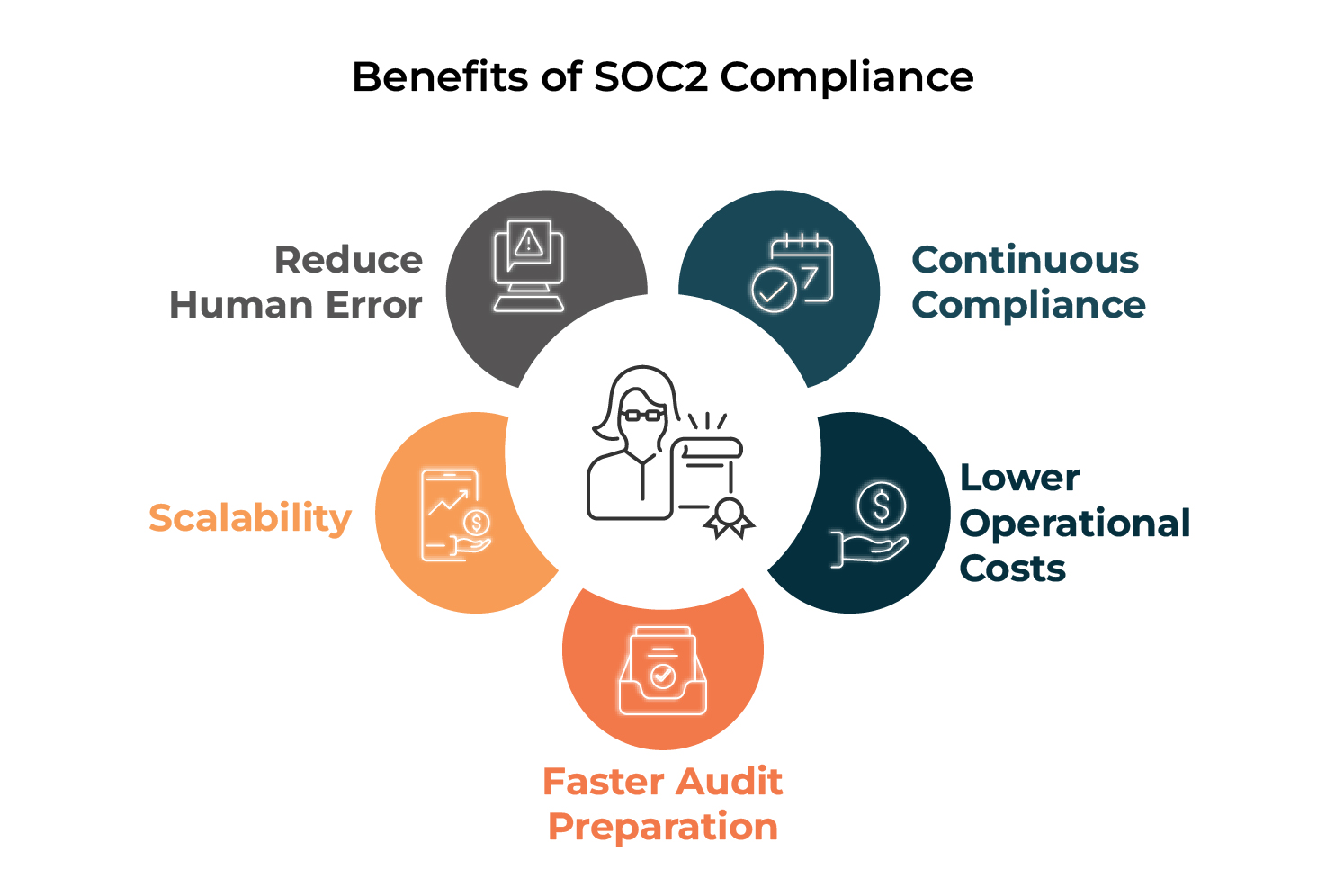
- Sooner Audit Preparation
With automated proof assortment and reporting, audits change into faster and extra streamlined. - Scalability
As your banking group grows, compliance automation scales with you—eliminating the necessity for a proportionate enhance in assets.
.fusion-body .fusion-builder-column-7{width:100% !necessary;margin-top : 0px;margin-bottom : 20px;}.fusion-builder-column-7 > .fusion-column-wrapper {padding-top : 0px !necessary;padding-right : 0px !necessary;margin-right : 1.92%;padding-bottom : 0px !necessary;padding-left : 0px !necessary;margin-left : 1.92%;}@media solely display and (max-width:1024px) {.fusion-body .fusion-builder-column-7{width:100% !necessary;order : 0;}.fusion-builder-column-7 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}@media solely display and (max-width:640px) {.fusion-body .fusion-builder-column-7{width:100% !necessary;order : 0;}.fusion-builder-column-7 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}
.fusion-body .fusion-flex-container.fusion-builder-row-8{ padding-top : 0px;margin-top : 0px;padding-right : 0px;padding-bottom : 0px;margin-bottom : 0px;padding-left : 0px;}
How SOC 2 Compliance Automation Helps the Banking Trade
With more and more digitized companies, on-line banking portals, cell apps, and cloud-hosted buyer information, making certain information safety and regulatory compliance is extra necessary than ever. Right here’s how automation with SOC 2 compliance helps:
-
Actual-time Threat Administration
Banks function in a high-risk surroundings and with automated SOC 2 compliance instruments banks can flag irregular exercise in actual time, corresponding to unauthorized entry to monetary data or coverage breaches.
A non-public sector financial institution lately built-in real-time monitoring instruments as a part of its automated SOC 2 compliance framework. If the system flagged an uncommon login try from a international IP handle accessing privileged person information after hours. The safety staff receives a right away alert, auto-blocks the entry, and initiates an investigation inside minutes—avoiding a possible breach and demonstrating proactive threat administration throughout their subsequent audit.
-
Operational Effectivity
Compliance officers and IT groups not must chase down logs and entry data throughout audits. Automated SOC 2 compliance in banking system helps gather and arrange these artifacts repeatedly.
Take for instance, a compliance officer at a co-operative financial institution beforehand spent days manually gathering proof from completely different sources—electronic mail approvals, entry logs, and coverage acknowledgments. After implementing an automatic SOC 2 compliance answer, this identical proof was repeatedly collected and arranged in a centralized dashboard. The officer might export all mandatory artifacts inside minutes, lowering audit preparation time by over 60%.
-
Improved Buyer Belief
Demonstrating a dedication to best-in-class safety requirements automated SOC 2 compliance enhances model credibility and reassures prospects that their monetary information is protected.
Any financial institution can implement an automatic SOC 2 compliance answer and start to showcase its compliance reviews and certifications on its web site and buyer communication channels. Because of this, the financial institution can expertise an accelerated enhance in new account openings over the subsequent quarter, with buyer surveys citing “information safety and transparency” as key choice drivers—displaying how automation straight contributed to belief and enterprise development.
-
Multi-Cloud Safety Administration
Many banks function in hybrid cloud environments. Automation of SOC 2 compliance permits centralized enforcement of safety insurance policies throughout AWS, Azure, and GCP.
Take for instance, a mid-sized Indian financial institution is increasing its digital choices together with cell banking, API integrations with fintech and cloud-based buyer onboarding programs. Throughout their final SOC 2 audit, they confronted points like:
- Delays in proof assortment
- Disparate logs from a number of programs
- Non-compliance flags on account of unmonitored entry rights
AutomationEdge Takes the Management
- Entry Controls: Bots repeatedly monitor person entry throughout functions and revoke extreme permissions routinely.
- Proof Assortment: RPA bots seize logs and screenshots from programs like Core Banking, CRM, and cloud platforms, storing them in a centralized repository.
- Actual-time Alerts: Any anomalous conduct triggers instantaneous alerts to the chance administration staff.
- Automated Experiences: Month-to-month compliance reviews are auto-generated, audit-ready, and aligned with SOC 2 framework.
.fusion-body .fusion-builder-column-8{width:100% !necessary;margin-top : 0px;margin-bottom : 20px;}.fusion-builder-column-8 > .fusion-column-wrapper {padding-top : 0px !necessary;padding-right : 0px !necessary;margin-right : 1.92%;padding-bottom : 0px !necessary;padding-left : 0px !necessary;margin-left : 1.92%;}@media solely display and (max-width:1024px) {.fusion-body .fusion-builder-column-8{width:100% !necessary;order : 0;}.fusion-builder-column-8 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}@media solely display and (max-width:640px) {.fusion-body .fusion-builder-column-8{width:100% !necessary;order : 0;}.fusion-builder-column-8 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}
.fusion-body .fusion-flex-container.fusion-builder-row-9{ padding-top : 0px;margin-top : 0px;padding-right : 0px;padding-bottom : 0px;margin-bottom : 0px;padding-left : 0px;}
Conclusion
SOC 2 compliance automation is a necessity for contemporary banking establishments aiming for development, belief, and resilience. From threat discount and value financial savings to audit readiness and real-time monitoring, automation ensures that banks keep forward of regulatory calls for whereas specializing in core banking operations. AutomationEdge offers end-to-end compliance automation capabilities, built-in with IT and enterprise programs to streamline governance and speed up audit-readiness.
.fusion-body .fusion-builder-column-10{width:100% !necessary;margin-top : 0px;margin-bottom : 20px;}.fusion-builder-column-10 > .fusion-column-wrapper {padding-top : 0px !necessary;padding-right : 0px !necessary;margin-right : 1.92%;padding-bottom : 0px !necessary;padding-left : 0px !necessary;margin-left : 1.92%;}@media solely display and (max-width:1024px) {.fusion-body .fusion-builder-column-10{width:100% !necessary;order : 0;}.fusion-builder-column-10 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}@media solely display and (max-width:640px) {.fusion-body .fusion-builder-column-10{width:100% !necessary;order : 0;}.fusion-builder-column-10 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}
.fusion-body .fusion-flex-container.fusion-builder-row-11{ padding-top : 0px;margin-top : 0px;padding-right : 0px;padding-bottom : 0px;margin-bottom : 0px;padding-left : 0px;}
Regularly Requested Questions
.fusion-accordian #accordion-23192-1 .panel-title a .fa-fusion-box{ colour: #ffffff;}.fusion-accordian #accordion-23192-1 .panel-title a .fa-fusion-box:earlier than{ font-size: 13px; width: 13px;}.fusion-accordian #accordion-23192-1 .panel-title a{font-size:18px;}.fusion-accordian #accordion-23192-1 .fa-fusion-box { background-color: #ff5700;border-color: #ff5700;}.fusion-accordian #accordion-23192-1 .panel-title a:hover, #accordion-23192-1 .fusion-toggle-boxed-mode:hover .panel-title a { colour: #005c7a;}.fusion-accordian #accordion-23192-1 .panel-title .energetic .fa-fusion-box,.fusion-accordian #accordion-23192-1 .panel-title a:hover .fa-fusion-box { background-color: #005c7a!necessary;border-color: #005c7a!necessary;}
.fusion-body .fusion-builder-column-11{width:100% !necessary;margin-top : 0px;margin-bottom : 20px;}.fusion-builder-column-11 > .fusion-column-wrapper {padding-top : 0px !necessary;padding-right : 0px !necessary;margin-right : 1.92%;padding-bottom : 0px !necessary;padding-left : 0px !necessary;margin-left : 1.92%;}@media solely display and (max-width:1024px) {.fusion-body .fusion-builder-column-11{width:100% !necessary;order : 0;}.fusion-builder-column-11 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}@media solely display and (max-width:640px) {.fusion-body .fusion-builder-column-11{width:100% !necessary;order : 0;}.fusion-builder-column-11 > .fusion-column-wrapper {margin-right : 1.92%;margin-left : 1.92%;}}
.fusion-body .fusion-flex-container.fusion-builder-row-12{ padding-top : 0px;margin-top : 0px;padding-right : 0px;padding-bottom : 0px;margin-bottom : 0px;padding-left : 0px;}
The put up What’s SOC 2 and all the things it’s essential to know! appeared first on AutomationEdge.